Video: What does advanced threat detection really look like in AustraliaVideo
🔍 What Does Advanced Threat Detection Really Look Like in Australia? Many Australian organisations believe they’ve achieved “advanced” threat detection—but are they actually prepared for today’s adversaries? In this video,…
What Does Advanced Threat Detection Really Look Like in Australia?
What Does Advanced Threat Detection Really Look Like in Australia? A critical lens on current practices, global parallels, and the road to true threat anticipation Introduction: The Myth of ‘Advanced’…
Exposed: What Your Network and Her Neck Have in Common
Why Threat Intelligence Alone Won’t Save You — And What Will The average organisation in Australia still believes it can buy its way to safety. A firewall here. An endpoint…
The CIO’s Guide to a Hackers’ Paradise: The All-Microsoft Tech Stack Gamble
The CIO’s Guide to a Hackers’ Paradise: The All-Microsoft Tech Stack GamblePicture this: You’re a CIO. Your budget is tighter than a new pair of jeans after Christmas, and your…
Unlocking Next-Level Threat Hunting
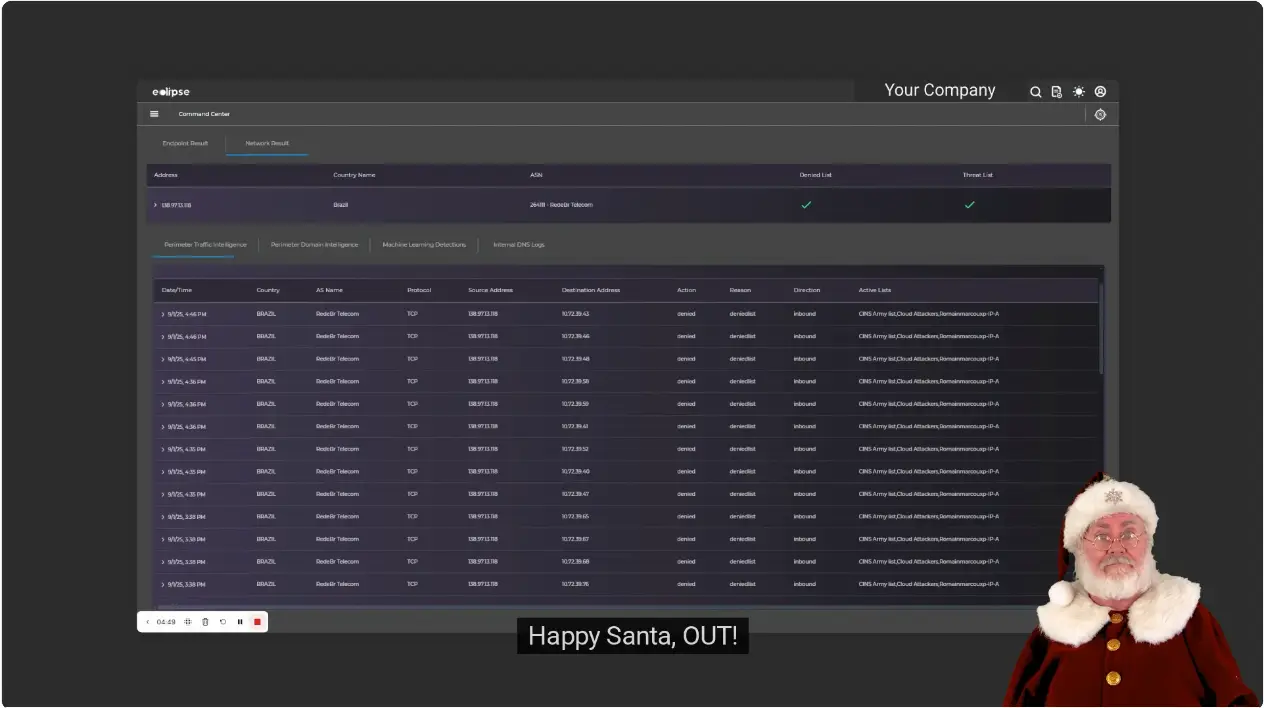
Unlocking Next-Level Threat Hunting with Forensic Depth Analysis and CyberStash Eclipse.XDR Cyber Defence Platform In today’s high-stakes cyber landscape, enterprises must adopt a proactive, multi-faceted approach to threat detection—one that…
Clogged Drains and Internet Pipes: A Sticky Situation You Don’t Want to Be in!
Clogged Drains and Internet Pipes A Sticky Situation You Don’t Want to Be in! Breach Prevention Advanced Threat Detection and Response Clogged Drains and Internet Pipes: A Sticky Situation You…
Cyber Risk Appetite vs. Business Survival: Striking the Perfect Balance
Cyber Risk Appetite vs. Business Survival: Striking the Perfect Balance Understanding an organisation’s risk appetite is critical for balancing security, operational efficiency, and business continuity. Risk appetite is not a…
Using CyberStash’s Eclipse.XDR to Search for IOCs
Learn how to efficiently search for threats within your environment using the Eclipse.XDR Cyber Defence platform. In this session, Sally, a cybersecurity analyst at CyberStash, demonstrates how to leverage indicators…
What does a Tesla and sophisticated malware have in common?
What does a Tesla and sophisticated malware have in common? Both are quiet, efficient, and designed with unparalleled precision. Tesla’s sleek electric vehicles redefine transportation with innovation and silence, while…
The Man in the Middle podcast: CyberStash Eclipse.XDR Cyber Defense Platform
I recently had the chance to speak at CyberCon, where I took the stage to talk about "Beyond Detection: Transforming Threat Intelligence into Actionable Attack Surface Reduction."The session was packed…
CyberCon Melbourne – November 2024: Transforming Threat Intelligence into Actionable Attack Surface Reduction
It was a privilege to present at CyberCon on "Beyond Detection: Transforming Threat Intelligence into Actionable Attack Surface Reduction." During the session, we explored the critical role of threat intelligence…
Podcast: Secrets to Operationalizing Threat Intelligence
In this episode of The Ryann Lofamia Podcast, Ryan Lofamia engages in a compelling conversation with Loris Minassian, the Founder and CEO of CyberStash, an innovative leader in the…
External Attack Surfaces in the Crosshairs: Pygmy Goat and the Shifting Cyber Threat Landscape
The Sophos XG firewall targeting in the Pacific Rim campaign, and the use of malware like Pygmy Goat, underscores a broader and highly significant issue: the management of the external…
How Small and Medium Businesses in Australia Can Avoid Common Cybersecurity Mistakes
In today's digital landscape, small and medium businesses in Australia are increasingly becoming targets for cyber criminals. These malicious actors often perceive small and medium enterprises as easy prey, exploiting…
The Fall of Constantinople: A Lesson in Cybersecurity Preparedness
On May 29, 1453, the city of Constantinople, once a bastion of Christian power and the capital of the Byzantine Empire, fell to the relentless assault of Sultan Mehmet II…
Don’t You Just Love Those Pesky Cybersecurity Folks?
Let’s face it: cybersecurity professionals can feel like the uninvited guests at a party. You know the type—always asking for more resources, pushing for that new license, and waving the…
Stay Safe Online with CyberStash Advanced Cybersecurity Solutions
In today's digital age, cyber security is more important than ever. Businesses of all sizes are at risk of cyber-attacks, which can have devastating consequences. CyberStash is a leading Australian…
Keeping Your Business Safe in the Digital Age: Cyber Security Solutions from CyberStash
In today's ever-evolving digital landscape, cyber security has become an essential concern for businesses of all sizes in Australia. With the constant rise of cyber threats, it's crucial to have…