
Experience Eclipse.XDR, the groundbreaking autonomous cyber defense platform revolutionizing protection, detection, threat hunting, and incident response. Engineered by Security Analysts for Security Analysts, Eclipse.XDR empowers your organization with unmatched security capabilities to proactively defend against evolving cyber threats. Ready to elevate your defense strategy and safeguard your business? Schedule a demo now to harness the unparalleled power of Extended Detection and Response (XDR).
Eclipse.XDR Live Demo
Force Multiplier
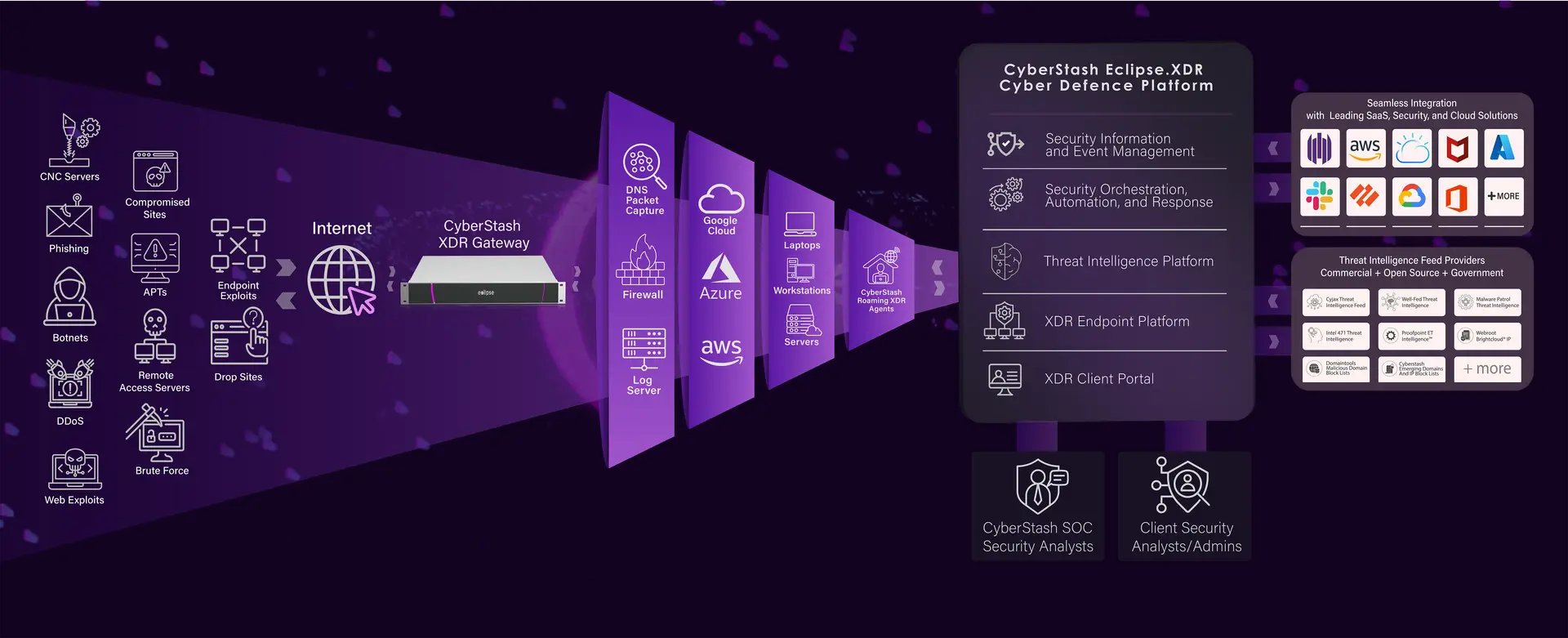
The independent cyber-defense platform eclipse.xdr acts as a force multiplier to dramatically reduce an organization’s exposure to cyber-attacks and minimize the likelihood of business impact after system compromise. Engrained into the platform is a defense-in-depth threat intelligence architecture that reduces an organization’s exposure to a massive number of cyber-threats, and a methodology that minimizes the breach dwell-time through periodic forensic-depth compromise assessments.

Design Principles
Leverage a defensive methodology that does not depend on prior knowledge of malicious code.
Cyber Defense Architecture
Forensic-Depth Compromise Assessments
Enrichment and Reverse Engineering Discovered Leads
Anomaly analysis of Operating System Artefacts
Discovery of High-risk Network Traffic Based on Intelligence, Machine Learning (ML), GEO-IP and ASN
Technology Stack
- Enriching discovery with intelligence
- Enriching discovery with dynamic analysis
- Searching for threat indicators
- Collecting additional forensic evidence
- Isolating an infected host
- Deleting a malicious file or registry key
- Killing a malicious process or service
- Removing a persistence mechanism
- Executing a PowerShell command
Network Incident Response Gateway
- Blocking the IP Address associated with the source of the attack.
- Ransomware TrackerBlocking the domains associated with the source of the attack.
- Blocking the country the attack originates from.
- Blocking the ASN the attack originates from.
Extended
Fortify your existing defenses with eclipse.xdr, the independent cyber defense platform that leverages multi-point telemetry to dramatically reduce your organization’s exposure to cyber-attacks while preventing business impact by automating threat detection and incident response.
Detection
Enrich endpoint and network telemetry with threat intelligence, forensic-depth compromise assessments, dynamic analysis and machine learning to expand your detection capability and achieve a zero-trust security architecture.
Response
Orchestrate incident response using automated risk-based decisions to optimize resources and inform periodic threat hunting and on-demand actions by the security analyst.
Every day, an unbelievable 850,000 new malicious IP addresses are launched, 8 billion spam and phishing attacks occur, and 30 to 50 million malicious domains exist at any one time.
Too often neutralising cyber threats is reactive and limited to single point-in-time analysis.
Enhance Your Security with Advanced XDR Solutions
In today’s complex threat landscape, advanced protection is essential for maintaining robust cybersecurity. At CyberStash, our Extended Detection and Response (XDR) services in Australia provide comprehensive advanced threat protection that integrates seamlessly with your existing infrastructure. We offer a sophisticated approach to SIEM in Australia, combining real-time threat detection, in-depth analytics, and rapid response to ensure your organization is fortified against emerging threats.
Our XDR solutions are designed to deliver exceptional protection not only within Australia but also on a global scale. Whether you require advanced threat protection services in Australia or need to extend your security capabilities worldwide, CyberStash’s global expertise ensures that you receive top-notch, scalable protection tailored to your business needs.
With CyberStash, you gain access to cutting-edge XDR and SIEM technologies that provide holistic and proactive security measures, empowering your organization to stay ahead of sophisticated cyber threats, wherever you operate.
To stay a step ahead of the adversary, continuous monitoring and coverage of the adversary, their turf and their tools are a necessity.
Eclipse.XDR empowers the collective threat intelligence gathered globally to detect and block known and emerging threats in real time and reduces an organization’s exposure to the staggering number of potential attackers.
Outcomes
Collection
Collection of forensic-level system information from all endpoints across the entire IT fleet
Forensic State Analysis
Validate every aspect of the system by going underneath higher-level Operating system APIs and working directly with volatile memory structures.
Enrichment
Inform discovery using Code Comparison, Machine Learning, Sandboxing, Threat Intelligence and
Stacking Techniques.
State-of-the-art
Cyber Security Platform
To stay ahead of threats, the methodology used must not depend on detection engines designed to catch the threat itself.
The capability used to support such a methodology must be designed to ‘catch all leads’ and then validate each one and provide a conclusive verdict of either ‘compromised’ or ‘not compromised’ without leaving any room for doubt.
How we do it?
eclipse.xdr protects organizations by harvesting and empowering a massive number of threat intelligence indicators and operationalizing these to block attacks in their tracks. Risk-based inbound and outbound policies add weighting to an indicator’s base-risk score to compound the level of threat to the organization if the traffic is associated with a high-risk ASN or high-risk country. Your organization’s exposure to cyber-threat is immensely reduced through this defensive methodology.
CyberStash establishes trust in an IT environment by carrying out 15 steps.
The process we follow is akin to that of a highly trained digital forensic analyst, however, we deliver our deep-level analysis at scale through automated host-level surveys before augmenting and enriching what we’ve discovered.
When delivered as a Managed Detection and Response (MDR) service, our security analysts then go over the endpoint meticulously to flag every operating system component as Verified Good, For Review, Potentially Unwanted or Verified Bad. We maintain a memory of these decisions and then work on all the net-new forensic leads we discover on subsequent assessments, thus enabling us to deliver a feasible and scalable service to any size enterprise.
